Abstract
- Apple AirTags supply a reasonably excessive diploma of safety, together with end-to-end encryption and anti-stalking options. On-line snooping is extraordinarily unlikely.
- You may have to safeguard your Apple Account, although, and ensure any machine logged into Discover My is about to auto-lock (comparatively) rapidly.
- Watch out about who you share AirTag location data with, and revoke entry if there are any worries about abusive or controlling habits.
In a number of quick years, Bluetooth trackers have gone from a brand new product class to a part of each day life for many individuals, in no small half due to the AirTag. Apple is an professional at promoting individuals on the advantages of its ecosystem, and talking as an proprietor of a number of AirTags myself, they are surely easy to make use of aside from the annoyance of swapping out their batteries at the least every year. It is best to not go overboard on monitoring for that cause.
Privateness, naturally, is among the issues try to be most involved about with any tracker. It is one factor to let advertisers know what metropolis you reside in — it is one other for a tool to be following your keys, health club bag, and even your automotive wherever you go. Here is what you must know in regards to the security of AirTags, together with some issues Apple would not inform you on its web site.
Associated
If you aren’t using Apple’s App Tracking Transparency, read this immediately
App Monitoring Transparency is an under-appreciated Apple software program ecosystem perk – here is what the characteristic entails, in addition to find out how to configure it.
Anti-stalking tech and extra
The very first thing to pay attention to is how AirTags work more often than not. Whereas they help ultra-wideband (UWB) monitoring at shut vary — a characteristic often called Precision Discovering — more often than not, they’re broadcasting occasional Bluetooth “pings,” that are picked up by iPhones, iPads, and Macs signed into Apple’s Find My community, whether or not they belong to you or not. That knowledge is then uploaded to Apple servers so it may possibly attain you through the Discover My app and web site. Which may sound scary at first, however the pings are anonymized, and the Discover My community makes use of end-to-end encryption. It will be extraordinarily tough for anybody to intercept helpful knowledge immediately, together with Apple.
Furthermore, the accuracy of Bluetooth monitoring relies on what number of Apple gadgets are round and when an AirTag was final capable of ping one. In case you drop your keys in Occasions Sq., you are going to get a comparatively exact location, as a result of there are virtually actually dozens of Apple gadgets passing by each minute. In case you drop these keys throughout a hike in rural Colorado, it might be hours or days earlier than somebody with an iPhone passes by to replace location data — within the interim, you will simply see the final place your individual iPhone detected them.
Folks can and have used AirTags to stalk individuals, because it’s comparatively simple to slide them into the crevices of garments, baggage, autos, and different objects. For a short time, this made AirTags extraordinarily controversial, though Apple has all the time been in a position to make use of the serial quantity and Apple Account related to an AirTag to assist police investigations. The state of affairs improved, fortunately, when Apple collaborated with Google on constructing anti-stalking options into each iOS/iPadOS and Android.
Within the case of a suspicious AirTag, make sure to doc every little thing.
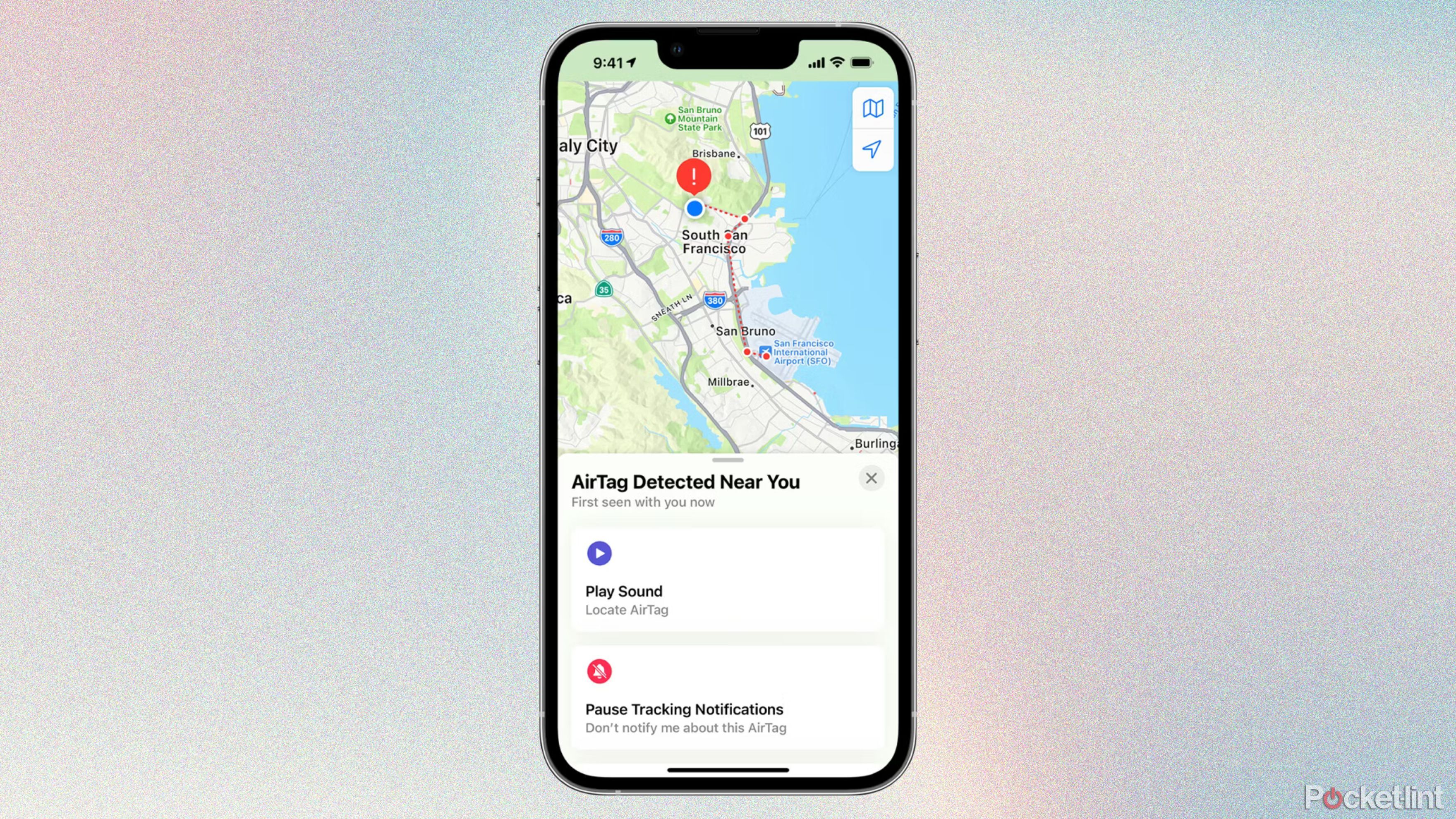
The result’s that if any Bluetooth tracker is following you with out its proprietor, it is best to see a notification in your iPhone, iPad, or Android. AirTags, at the least, also needs to play a sound, and in case you obtain a notification a few tracker, the Discover My app will show choices to play that sound once more and/or provoke Precision Discovering (when out there). Bear in mind that some stalkers are good sufficient to interrupt the speaker on a tracker earlier than planting it — so if Precision Discovering is not doable, you will have to look the onerous manner.
In case you do encounter an unknown AirTag, you possibly can maintain any NFC-equipped telephone as much as it to get its serial quantity and the final 4 digits of its proprietor’s telephone quantity. If it is marked as misplaced, you also needs to see a message from its proprietor, presumably with additional contact data.
Within the case of a suspicious AirTag, make sure to doc every little thing — that features not simply the information above, however when and the place you discovered it, and any path historical past proven in Discover My. Take images and screenshots you possibly can hand over to police. As soon as that is finished, although, make sure to disable the AirTag by opening it up and eradicating its battery. You also needs to in all probability transfer to a secure location, since there is not any telling if the stalker will come by to research.
Associated
Find My Device: a lifesaver or a digital leash?
It is in all probability price maintaining, however there are eventualities the place opting out could be sensible.
Ought to I nonetheless be frightened about AirTag safety?
What Apple would not say, and the ultimate verdict
As you might have gathered, the specter of AirTag stalking is low, however nonetheless non-zero. Sure, your iPhone, iPad, or Android machine ought to notify you in case you’re being adopted by an unknown tracker, however a very aggressive stalker could be shut and quick sufficient to succeed in you earlier than you reply. In case you see a tracker notification in your telephone, take it significantly.
You also needs to be considered about sharing AirTag places with buddies, household, or companions through Discover My. Normally, in fact, these are individuals you possibly can belief — but when they flip abusive or controlling, bear in mind to revoke their entry instantly. At all times suppose twice about sharing with somebody you’ve got solely lately met, regardless of how effectively you are getting alongside.
In case you’re ready for all of this, it is best to really feel pretty assured about utilizing AirTags.
As for different events intercepting your knowledge, the principle factor you must fear about is somebody hijacking your Apple Account. If they will uncover or brute-force your login data, they will entry Discover My, and pinpoint the situation of each merchandise listed — not simply your AirTags. Due to this, it is important to make use of a posh password, and keep away from sharing your login with anybody you would not belief together with your life. You would possibly need to keep away from utilizing Discover My in any respect if there is a threat an authoritarian authorities would possibly seize you and your gadgets to search out family members.
Be aware of bodily machine safety, too. Any machine logged into Discover My ought to have a passcode or password enabled, and be set to auto-lock after a set period, the shorter the higher (inside cause). That second step would possibly really feel like overkill, but when a tool is snatched from you earlier than you possibly can manually lock it, they might have free rein in Discover My (and different apps) lengthy sufficient to do injury. At your office, somebody may wander by your empty workplace, scour Discover My in your iPhone or pc, then disappear earlier than you’ve got returned from the lavatory.
In case you’re ready for all of this, although, it is best to really feel pretty assured about utilizing AirTags. You’re opening a brand new realm of issues — however the identical is true of any machine that talks to the web, and most of us aren’t about to go dwell in a shack within the woods due to our telephones and good bulbs.
Associated
The lowdown on Apple’s Activation lock: 4 things you need to know
It is normally an important security characteristic, nevertheless it can be a hurdle.
Trending Merchandise

Acer Aspire 3 A315-24P-R7VH Slim Laptop computer | 15.6″ Full HD IPS Show | AMD Ryzen 3 7320U Quad-Core Processor | AMD Radeon Graphics | 8GB LPDDR5 | 128GB NVMe SSD | Wi-Fi 6 | Home windows 11 Residence in S Mode

LG 27MP400-B 27 Inch Monitor Full HD (1920 x 1080) IPS Display with 3-Side Virtually Borderless Design, AMD FreeSync and OnScreen Control – Black

Thermaltake V250 Motherboard Sync ARGB ATX Mid-Tower Chassis with 3 120mm 5V Addressable RGB Fan + 1 Black 120mm Rear Fan Pre-Installed CA-1Q5-00M1WN-00

TP-Hyperlink AXE5400 Tri-Band WiFi 6E Router (Archer AXE75)- Gigabit Wi-fi Web Router, ax Router for Gaming, VPN Router, OneMesh, WPA3

CORSAIR iCUE 4000X RGB Tempered Glass Mid-Tower ATX PC Case – 3X SP120 RGB Elite Followers – iCUE Lighting Node CORE Controller – Excessive Airflow – Black

Wireless Keyboard and Mouse Combo, EDJO 2.4G Full-Sized Ergonomic Computer Keyboard with Wrist Rest and 3 Level DPI Adjustable Wireless Mouse for Windows, Mac OS Desktop/Laptop/PC